My opening blog argued that cyberwarfare has been affecting the World for some time and is here to stay. It is evolving and history in the making, forever updating itself … not unlike one’s apple products. Writing this blog on Cyberwarfare has been an enjoyable surprise, although some of my conclusions are profoundly worrying. It has been enjoyable because it has been interesting; my early thoughts have been confirmed. The surprise was threefold: the amount of regular reporting by the media about cyberwarfare related matters; that inter-state cyberwarfare has been going on longer than I realised; and the unexpected directions some of my research took me.
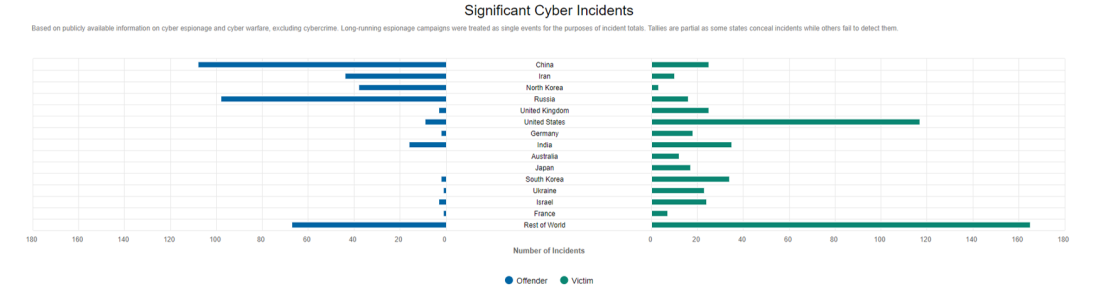
My blog’s focus was intended to be on ‘state organised or sponsored cyberwarfare’. It is not melodramatic to state that the world is now at war because, without doubt, nations are now waging silent, seemingly bloodless wars on one another (on one’s ‘allies’ even) via the medium of the internet and cyberspace. Crucially there is an unstated ‘Cold War’ ongoing between the major nations of the world and, with it, a digital arms race seeking to exploit data. My blogs have covered cyber incidents involving Russia, China, the USA and surprisingly, yet unsurprisingly, Britain. In October alone the US had nine significant cyber incidents (which we know about), some of which I covered in my blogs, the list of which I have provided below along with a link for the whole list dating back to 2006. NATO is currently operating its biggest ‘cyber warfare exercise’ in Estonia (one of Russia’s many neighbours) after a year of attacks on ‘sports bodies, the U.S. Democratic Party and the world chemical weapons watchdog in the Netherlands’, by the Kremlin or Russian linked hacking groups.

I put forward a definition and model of cyberwarfare, postulating that cyberwarfare encompasses both non-kinetic and kinetic warfare (without doubt it does). I stand by my definition (Cyberwarfare is non-kinetic and kinetic warfare in cyberspace) and I would not make any significant change to the model as I believe it explains cyberwarfare well conceptually. However, if I were to tackle the subject in more depth, the simplicity of this model would be too basic and it would need to include more sub-branches
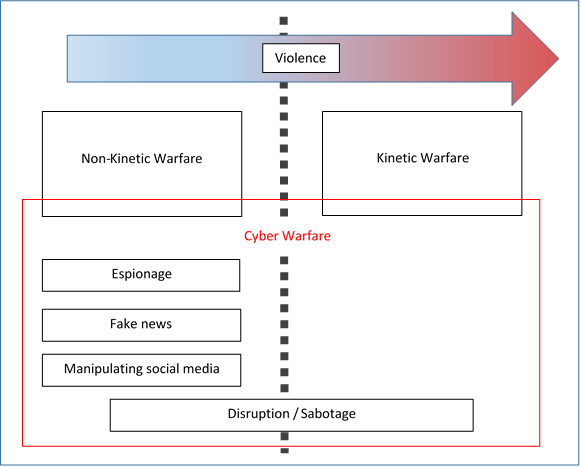
Cyberwarfare – a simple model
As cyberwarfare evolves and the human race changes (declines in some respects), cyberwarfare using artificial intelligence and robotics will change the nature of kinetic warfare profoundly by potentially removing the human element from direct face-to-face combat. Cyberwarfare is already the central, unifying means of conducting war and in the Clausewitzian sense is absolutely a means for the major world states to conduct war in order to achieve their political aims. This ‘cyber fighting’ is unseen and ungoverned by the ethical rules of war as we know them. If ‘all out’ war breaks out, attacks on Critical National Infrastructure (CNI) could make life a misery for large swathes of the human population, done in pursuit of political aims. All of this took me to my most worrying conclusion, which is that liberal democracy as we know it and hold dear is threatened and could be a shell of itself in less than fifty years. This could be the outcome of a cultural clash between China and the West. China will use all means, including making full use of cyberspace, to achieve its strategic aim of political, social, economic and military dominance.
China’s intentions are outside the scope of this report, but cyber ethics are not. The world is at a crossroads regarding cyberspace and thus cyber warfare. Traditional warfare has the Geneva Convention to at least give the impression that warfare adheres to a set of basic rules. Currently there is little to no internet oversight, with every attempt at regulation failing. This means that nations can operate in cyberspace with almost no restrictions, allowing them to perpetrate attacks they could not necessarily commit if they were fighting a conventional, ‘old fashioned’, war. Furthermore this detaches and desensitises humans conducting such wars, potentially making them less morally conscious about their cyber attacks. Retaliating is not easy where there is no direct physical presence and electronic tracks can be covered. Moreover it is significantly cheaper to use a computer to launch an attack than to use, say, an F-35 jet; the destructive impact of the jet could be less than that of a cyber attack on CNI.
A French official commented “The internet is a space currently managed by a technical community of private players. But it’s not governed. So now that half of humanity is online, we need to find new ways to organize the internet … Otherwise, the internet as we know it today — free, open and secure — will be damaged by the new threats.” That is the conundrum: how to retain a free and open internet (a good thing) yet how to police attacks going on unseen in cyberspace? More and more people (and more significantly, businesses, governments and their armies) are dependent on the internet to the point of no return to old ways of working and living lives, with scope for cyberattacks to become more ‘frequent, complex, destructive and coercive’. I cannot see the World’s leaders talking about governing cyberwarfare, although over the past couple of months there have been several calls for internet reform or tighter cyber security. The most notable calls both came in November 2018, coming from France and China, motivated by completely different reasons and neither gaining support from major powers such as the US or Russia. Nothing is therefore likely to come of these proposals in the short term, but we have to hope that this will change in the long term.
I therefore conclude that cyberwarfare as a means of conducting non-kinetic asymmetric warfare is now the norm and here to stay. It is also changing the nature of kinetic warfare profoundly, possibly to the extent that kinetic warfare will become a sub-set of cyberwarfare. Cyberwarfare’s legitimacy as a means of war has however yet to be established.
Webography:
Centre for Strategic & International Studies, Significant Cyber Incidents (2018),<https://csis-prod.s3.amazonaws.com/s3fs-public/181101_Significant_Cyber_Events_List.pdf?hsZtm10X2Ery9_CD.a2FYbE6ti..tQuu> [accessed 03/12/2018]
Damon Wake, NATO Tests Electronic Defenses as Cyber Warfare Threat Grows (2018),<https://www.military.com/daily-news/2018/12/01/nato-tests-electronic-defenses-cyber-threat-grows.html> [accessed 03/12/2018]
Cate Cadell, China’s Xi calls for global cooperation to create ‘fairer’ internet (2018),<https://www.reuters.com/article/us-china-cyber/chinas-xi-calls-for-global-cooperation-to-create-fairer-internet-idUSKCN1NC0CG> [accessed 03/12/2018]
Joseph Archer, US, Russia and China refuse to back French cybersecurity initiative (2018),<https://www.telegraph.co.uk/technology/2018/11/12/us-russia-china-refuse-back-french-cybersecurity-initiative/> [accessed 03/12/2018]